security vulnerabilities, two of which affect its Linux client that
could have allowed an attacker with access to a compromised system
to read and exfiltrate Zoom user data—and even run stealthy malware
as a sub-process of a trusted application.
According to cybersecurity researcher Mazin Ahmed[1], who presented his
findings[2] at DEF CON 2020
yesterday, the company also left a misconfigured development
instance exposed that wasn’t updated since September 2019,
indicating the server could be susceptible to flaws that were left
unpatched.
After Ahmed privately reported the issues to Zoom in April and
subsequently in July, the company issued a fix on August 3 (version
5.2.4).
attacker would need to have already compromised the victim’s device
by other means. But that doesn’t take away the significance of the
flaws.
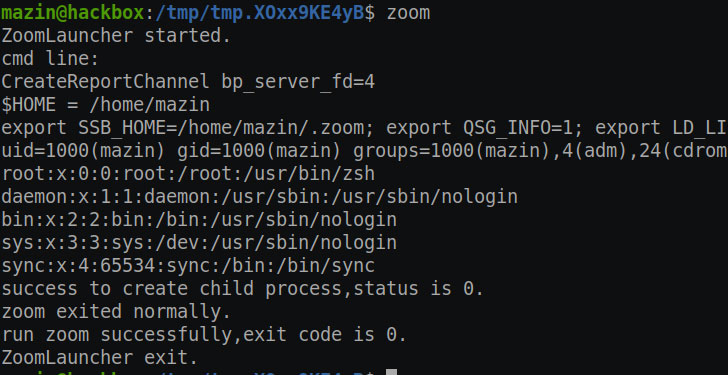
In one scenario, Ahmed uncovered an issue with the Zoom Launcher
for Linux that could allow an adversary to run unauthorized
software owing to the manner it launches the “zoom” executable.
“This breaks all of the protection of application whitelisting,
allows malware to run as a subprocess of a trusted vendor (Zoom),
and is a bad design/security practice by all means,” Ahmed said in
an analysis.
victim’s machine can read and exfiltrate Zoom user data and
configuration by navigating to the local database and even
accessing chat messages stored on the system in
plaintext format.
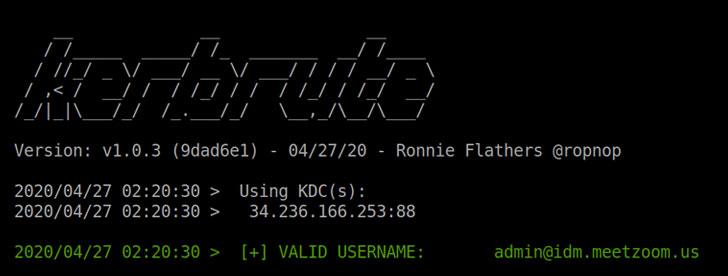
Two other flaws involved an externally accessible Kerberos
authentication service (“ca01.idm.meetzoom.us”) and a TLS/SSL issue
that lets malware inject custom certificate fingerprints into the
local Zoom database.
“This is per user certificate pinning and intentionally allows for
the user to allow custom certificates,” Zoom said of the
certificate injection flaw. “The user can write to their own
database, but no other non-root users can. It’s common best
practice to have user applications run at their privilege level, as
requiring Zoom to run as root would introduce unnecessary security
risks to Zoom and our customers.”
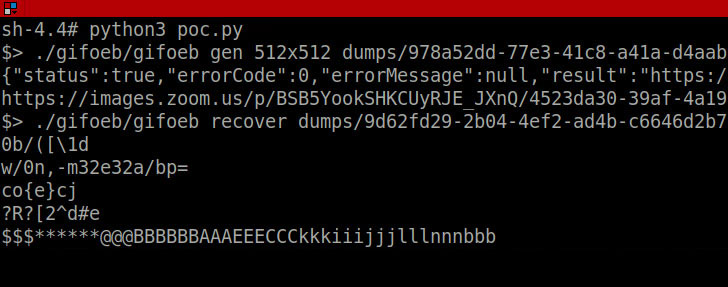
But it gets more interesting. Ahmed went on to highlight a
memory leak vulnerability by exploiting the profile picture feature
on Zoom to upload a malicious GIF image, download the rendered
file, and extract data from it to leak portions of system
memory.
was not a memory leak but just our image utility’s best effort at
converting a malformed gif into a jpeg,” the company said.
Although Ahmed believes this to be a consequence of a known flaw
in ImageMagick[4]
image conversion software (CVE-2017-15277[5]), Zoom has said it
doesn’t use the utility to convert GIFs uploaded as profile
pictures into JPEG format.
Kerberos authentication server to prevent brute-force attacks,
while also acknowledging that it’s working on addressing the lack
of encryption while storing the chat logs.
It’s recommended that users update Zoom to the latest version to
mitigate any risk arising out of these issues.
The development came as the company resolved a security
flaw[6] last month. It allowed
attackers to crack the numeric passcode used to secure private
meetings on the platform and eavesdrop on participants.
References
- ^
Mazin Ahmed
(twitter.com) - ^
presented his findings
(mazinahmed.net) - ^
chat messages
(zoom.us) - ^
ImageMagick
(imagemagick.org) - ^
CVE-2017-15277
(github.com) - ^
resolved a security flaw
(thehackernews.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/5X4byI1leOQ/zoom-software-vulnerabilities.html